4.2 KiB
Wg Gen Web
Simple Web based configuration generator for WireGuard.
Why another one ?
All WireGuard UI implementations are trying to manage the service by applying configurations and creating network rules. This implementation only generates configuration and its up to you to create network rules and apply configuration to WireGuard. For example by monitoring generated directory with inotifywait.
The goal is to run Wg Gen Web in a container and WireGuard on host system.
Features
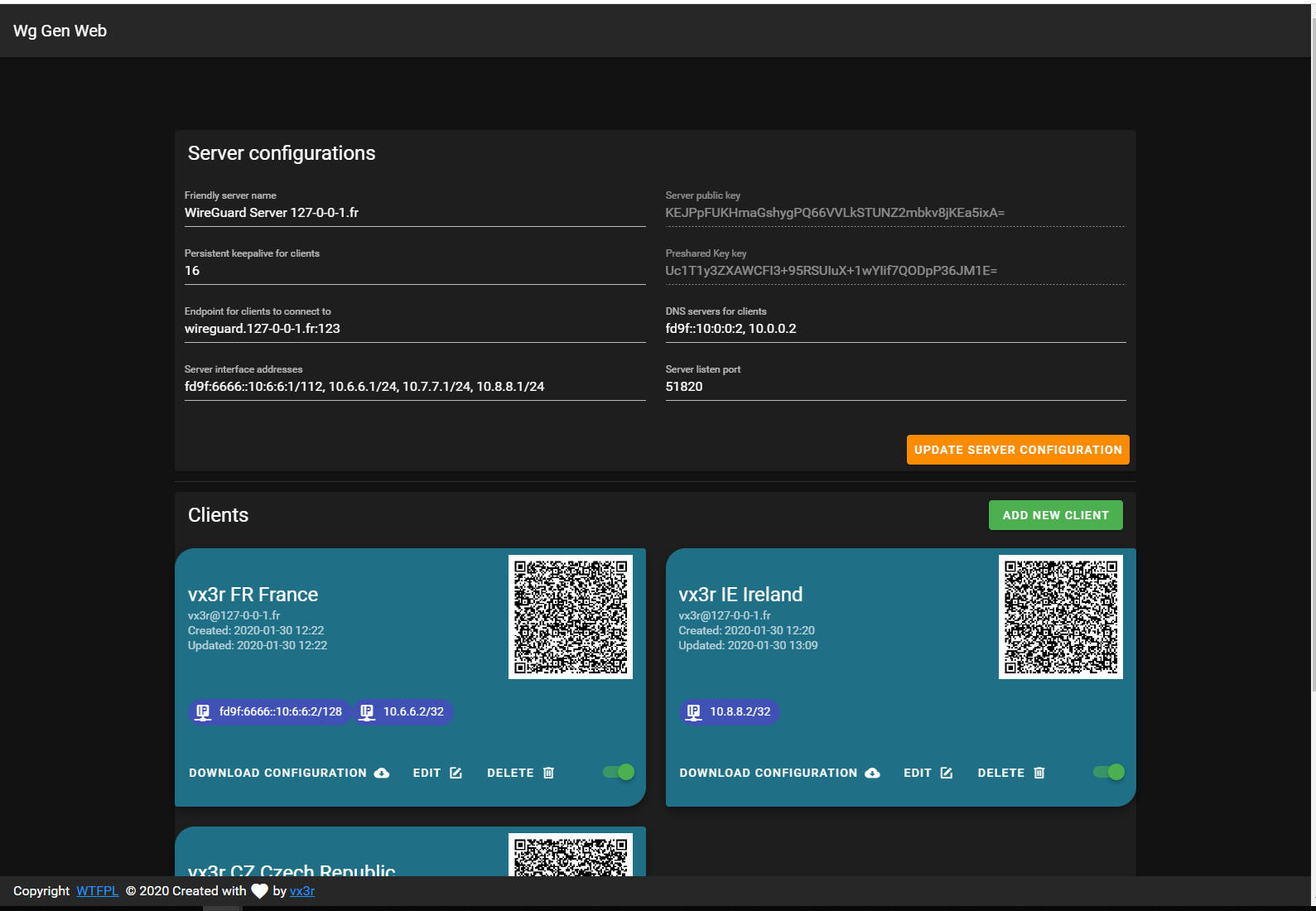
- Self-hosted and web based
- Automatically select IP from the netowrk pool assigned to client
- QR-Code for convenient mobile client configuration
- Enable / Disable client
- Generation of
wg0.confafter any modification - Dockerized
- Pretty cool look
Running
The easiest way to run Wg Gen Web is using the container image
docker run --rm -it -v /tmp/wireguard:/data -p 8080:8080 -e "WG_CONF_DIR=/data" vx3r/wg-gen-web:latest
Docker compose snippet
version: '3.6'
services:
wg-gen-web:
image: vx3r/wg-gen-web:latest
container_name: wg-gen-web
restart: unless-stopped
expose:
- "8080/tcp"
environment:
- WG_CONF_DIR=/data
- WG_INTERFACE_NAME=wg0.conf
volumes:
- /etc/wireguard:/data
Please note that mapping /etc/wireguard to /data inside the docker, will erase your host's current configuration.
If needed, please make sure to backup your files from /etc/wireguard.
A workaround would be to change the WG_INTERFACE_NAME to something different, as it will create a new interface (wg-auto.conf for example), note that if you do so, you will have to adapt your daemon accordingly.
Automatically apply changes using systemd
Using systemd.path monitor for directory changes see systemd doc
# /etc/systemd/system/wg-gen-web.path
[Unit]
Description=Watch /etc/wireguard for changes
[Path]
PathModified=/etc/wireguard
[Install]
WantedBy=multi-user.target
This .path will activate unit file with the same name
# /etc/systemd/system/wg-gen-web.service
[Unit]
Description=Restart WireGuard
After=network.target
[Service]
Type=oneshot
ExecStart=/usr/bin/systemctl restart wg-quick@wg0.service
[Install]
WantedBy=multi-user.target
Which will restart WireGuard service
Automatically apply changes using inotifywait
For any other init system, create a daemon running this script
#!/bin/sh
while inotifywait -e modify -e create /etc/wireguard; do
wg-quick down wg0
wg-quick up wg0
done
How to use with existing WireGuard configuration
After first run Wg Gen Web will create server.json in data directory with all server informations.
Feel free to modify this file in order to use your existing keys
What is out of scope
- Generation or application of any
iptablesornftablesrules - Application of configuration to WireGuard by Wg Gen Web itself
TODO
- Multi-user support behind Authelia (suggestions / thoughts are welcome)
- Send configs by email to client
License
- Do What the Fuck You Want to Public License. LICENSE-WTFPL or http://www.wtfpl.net





